Best Practices for Secure Database Application Development
Quick Summary
In today’s digital landscape, where data is often considered the most valuable asset, ensuring the security of database applications is paramount. From small businesses to large enterprises, the need to protect sensitive information from cyber threats has never been more critical. In this comprehensive guide, we will delve into the best practices for secure database application development, equipping you with the knowledge and tools necessary to safeguard your data assets effectively.
Understanding the Importance of Secure Database Application Development
Before diving into the best practices, it’s crucial to understand why secure database application development is essential. Database applications serve as repositories for valuable data, including customer information, financial records, and intellectual property. A breach in security could lead to severe consequences, including financial losses, reputational damage, and legal repercussions. By implementing robust security measures during the development phase, organizations can mitigate these risks and protect their data assets.
Best Practices for Secure Database Application Development
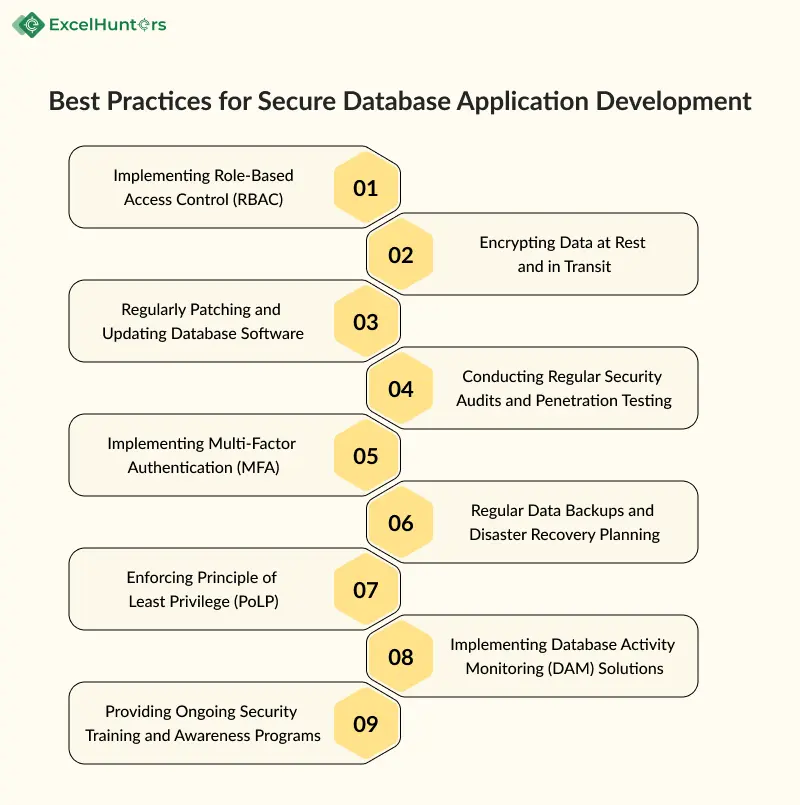
1. Implementing Role-Based Access Control (RBAC)
One of the fundamental principles of secure database application development is implementing Role-Based Access Control (RBAC). RBAC restricts access to sensitive data based on the roles and responsibilities of individual users within the organization. By defining granular permissions and access levels, organizations can ensure that only authorized personnel can view, modify, or delete sensitive information. This helps prevent unauthorized access and reduces the risk of data breaches.
2. Encrypting Data at Rest and in Transit
Encrypting data both at rest and in transit is essential for maintaining the confidentiality and integrity of sensitive information. At rest, data encryption protects stored data from unauthorized access by encrypting it using cryptographic algorithms. Similarly, encrypting data in transit ensures that information remains secure while being transmitted between servers, applications, and users. Implementing strong encryption protocols such as AES (Advanced Encryption Standard) helps safeguard data against eavesdropping and interception by malicious actors.
Encrypting data both at rest and in transit is essential for maintaining the confidentiality and integrity of sensitive information. At rest, data encryption protects stored data from unauthorized access by encrypting it using cryptographic algorithms. Similarly, encrypting data in transit ensures that information remains secure while being transmitted between servers, applications, and users. Implementing strong encryption protocols such as AES (Advanced Encryption Standard) helps safeguard data against eavesdropping and interception by malicious actors.
Keeping database software up to date with the latest security patches and updates is critical for addressing known vulnerabilities and weaknesses. Hackers often exploit outdated software to gain unauthorized access to databases and exploit security flaws. By regularly patching and updating database software, organizations can close security gaps and fortify their defenses against emerging threats. Automated patch management tools can streamline the process and ensure timely updates without disrupting operations.
4. Conducting Regular Security Audits and Penetration Testing
Regular security audits and penetration testing are essential components of a proactive security strategy. Security audits involve reviewing database configurations, access controls, and user permissions to identify potential vulnerabilities and compliance issues. Penetration testing, on the other hand, involves simulating cyber attacks to assess the effectiveness of security controls and identify weaknesses in the system. By conducting regular audits and penetration tests, organizations can identify and address security gaps before they can be exploited by malicious actors.
5. Implementing Multi-Factor Authentication (MFA)
Multi-Factor Authentication (MFA) adds an extra layer of security by requiring users to provide multiple forms of authentication before accessing sensitive data. This typically involves combining something the user knows (such as a password) with something they have (such as a mobile device or security token) or something they are (such as biometric data). By implementing MFA, organizations can significantly reduce the risk of unauthorized access, even if a user’s credentials are compromised.
6. Regular Data Backups and Disaster Recovery Planning
Data backups and disaster recovery planning are essential for ensuring business continuity in the event of a security incident or data breach. Regularly backing up critical data to secure offsite locations helps organizations recover quickly from data loss or corruption. Additionally, developing a comprehensive disaster recovery plan that outlines procedures for responding to security incidents, restoring data, and minimizing downtime is crucial for minimizing the impact of potential breaches.
7. Enforcing Principle of Least Privilege (PoLP)
The Principle of Least Privilege (PoLP) is a security best practice that restricts user access to the bare minimum permissions necessary to perform their job functions. By limiting user privileges, organizations can reduce the risk of accidental or intentional misuse of sensitive data. Implementing PoLP ensures that users only have access to the information and resources required to fulfill their roles, minimizing the potential impact of security incidents.
8. Implementing Database Activity Monitoring (DAM) Solutions
Database Activity Monitoring (DAM) solutions play a crucial role in detecting and preventing unauthorized access and suspicious activities within database environments. DAM solutions monitor database transactions and user activities in real-time, alerting administrators to potential security threats such as SQL injection attacks, unauthorized data access attempts, and anomalous behavior. By implementing DAM solutions, organizations can gain visibility into their database activities and proactively identify and respond to security incidents before they escalate into major breaches.
9. Providing Ongoing Security Training and Awareness Programs
In addition to implementing technical security measures, organizations should invest in ongoing security training and awareness programs for employees. Human error remains one of the leading causes of data breaches, with employees inadvertently falling victim to phishing attacks, social engineering tactics, and other cyber threats. By educating employees about security best practices, recognizing common attack vectors, and promoting a culture of vigilance, organizations can empower their workforce to become the first line of defense against cyber threats. Regular security training sessions, simulated phishing exercises, and awareness campaigns can help reinforce security protocols and instill a security-conscious mindset across the organization.
Conclusion
In conclusion, securing database applications is essential for protecting sensitive data assets from cyber threats and unauthorized access. By implementing best practices such as Role-Based Access Control (RBAC), data encryption, regular patching and updates, security audits, multi-factor authentication (MFA), data backups, disaster recovery planning, and Principle of Least Privilege (PoLP), organizations can enhance their security posture and mitigate the risk of data breaches. Prioritizing security during the development phase is key to safeguarding valuable data assets and maintaining customer trust in an increasingly digital world.
To inquire about database application development services, please contact Excelhunters.
Looking for
Consultations?Our Expertise
- 8 + years of experience
- Adept Developers
- Excel at Agile Development
- Cost-Effective